A handy trio of tools for protecting your privacy
Encrypting in Transit: Tor
Anonymizing tools conceal your Internet activities so that no one will be able to trace or analyze where you go on the web. One powerful option for protecting data in transit is Tor [4], a sophisticated peer-based virtual private network designed to guard you and your information against profiling from any entity. Tor uses a distributed, peer-based network. Each computer that actively participates on the Tor network is called a relay. It is possible to connect to the Tor network as a mere user or as a relay.
With Tor, your network traffic is encrypted using public key encryption then routed and forwarded on a near-random basis through the Tor network. As a result, it is quite difficult for anyone to determine the sites you have visited. Ironically, Tor was created by the United States Navy. Called the "Onion Routing Project," Tor was designed to help protect Navy traffic from snooping.
A Tor network is a distributed virtual network designed to do two things: First, Tor encrypts traffic. Second, it randomizes traffic so that it is more difficult for any entity to analyze it. Tor is quite successful, and several government entities have gone on record recently, noting that the Tor network is quite good at randomizing and anonymizing traffic. Although governments regularly capture Tor-based traffic, they tend to find that traffic analysis and decryption of Tor data is fairly difficult.
How Does Tor Work?
Tor is the Napster or LimeWire of VPN servers: All you have to do is install some software, join with the Tor network, and you are on your way to encrypting and anonymizing your network.
You'll need to configure your web browser to access your system as you would any proxy server, such as Squid. Tor uses the SOCKS protocol for local network connections. This means when you configure your browser's proxy server settings, you'll want to use the SOCKS protocol and specify the port (usually TCP 9050).
The easy way to join up with a Tor network is to use the Tor Browser Bundle (TBB), which you can download from the Tor site. Simply download the software and participate in the Tor virtual private network scheme. The hard way is more interesting to me, because it allows you to contribute to the overall network. The hard way involves connecting to the Tor network as a relay, which helps add more randomization to the network.
To get started, download the Tor package using either the available tarball or the package available from your system repository. For example, I was able to download a copy of Tor using apt-get on my Ubuntu system without having to update any of the standard repositories. If you are using Tor to simply connect to the network, install the binary and use a system script to start the service (Listing 1).
Listing 1
Starting the Tor Service
When Tor runs in default mode, it listens for connections from your local machine on TCP port 9050. This port will accept only connections from your local machine. Once Tor is running, you should check its log files to make sure it has connected with the overall Tor network (Listing 2).
Listing 2
Tor Log File
Listing 2 shows that Tor has gone out to find relays on the Internet. Because I made sure my firewall software wasn't blocking Tor-based connections, the process went quite quickly.
Your Browser as a Tor Client
To use Tor, you will need to configure your browser for a proxy server. In Firefox, go to Edit | Preferences. Then, click on the Advanced tab, then click on the Settings tab. You can then enter the SOCKS configuration information, as shown in Figure 3.
The steps for configuring Opera, Chrome, or another browser are similar. Simply specify the correct SOCKS information. Once you have configured your browser, restart it. Then, point your web browser to the following URL to confirm that your system is communicating across Tor's relay network:
https://check.torproject.org
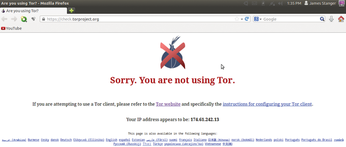
If your browser is not using the Tor network, you'll get a screen similar to Figure 4.
If your system and browser are properly configured and running, you will see the confirmation screen shown in Figure 5.
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.
-
New Pentesting Distribution to Compete with Kali Linux
SnoopGod is now available for your testing needs