Improve the way you work with Secure Shell
X, Please!
SSH can transfer graphical applications that are running on a remote computer to your own desktop. Assuming the SSH server on the other side allows X-forwarding (X11Forwarding yes in /etc/ssh/sshd_config) and the xauth package is installed, users can launch X11 programs on the remote machine and control them locally as a one off using ssh -X or permanently with an entry in the configuration file (ForwardX11 yes).
The whole thing becomes interesting when several computers are involved. Let's assume that host1 is allowed to access host2, and host2 can access host3, but a direct connection between host1 and host3 is not possible. Instead of multiple commands, users can type a single command (Figure 2):
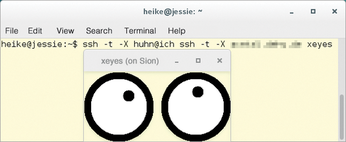 Figure 2: The xeyes program runs on the third host named Sion; however, the display appears in the graphical interface of the first computer (jessie).
Figure 2: The xeyes program runs on the third host named Sion; however, the display appears in the graphical interface of the first computer (jessie).
ssh -t -X host2 ssh -t -X host3 xeyes &
This is where you use the -t option (see the "On My Mark!" section). If an alias is defined in the configuration file, you can define the option ForwardX11 yes for host2 and host3. The third computer is also given instructions for the ProxyCommand (Listing 4).
Listing 4
X11 forwarding for multiple hosts in ~/.ssh/config
Secure Shell routes other TCP connections through a secure tunnel, if desired. Much like a proxy, SSH accepts the connection on a port on one side and links it to a port on the remote side.
Into the Pipe
Port forwarding works in both directions. Local port forwarding is enabled with the -L option and forwards a connection that arrives on an arbitrary local port through the SSH tunnel to a port on a remote server:
ssh -L <Local_port>:localhost:<Remote_port> <User>@<Remote_host>
Users can use such a tunnel to lift restrictions at the opposite end and, for example, reach a remote MySQL server that only listens to local connections (bind-address = 127.0.0.1) from the local computer (Figure 3).
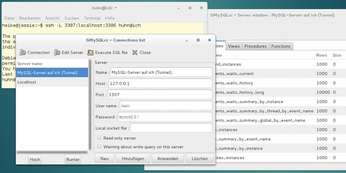 Figure 3: In the graphical MySQL client, users define 127.0.0.1 as the address of the remote MySQL server and the port number specified in the tunnel (3307 here).
Figure 3: In the graphical MySQL client, users define 127.0.0.1 as the address of the remote MySQL server and the port number specified in the tunnel (3307 here).
Tunneling is also possible in the opposite direction: In remote port forwarding, the connection arrives at a port on the remote computer, and the data are routed through the SSH tunnel to any port on the client side. Users can take advantage of the feature to share a service offered by a computer on the local network with others outside the LAN.
Instead of -L, the option used is -R.
ssh -R <Remote_port>:localhost:<Local_port> <User>@<Remote_host>
To make this happen, the GatewayPorts yes option must be set on the SSH server at the other end so that the remote computers can connect to local, forwarded ports. Figure 4 shows an example in which the web server (port 80), a Raspberry Pi (which is available only on the local network) is connected via an SSH tunnel to port 9000 on a remote server. The remote server has a public IP address, so the web server using port 9000 is now also reachable from the outside.
If you want to define the settings for one or more SSH tunnels in the configuration file; Listing 5 shows an example.
Listing 5
Local/remote port forwarding in ~/.ssh/config
Infos
- Man pages for OpenSSH: https://www.openssh.com/manual.html
« Previous 1 2
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.
-
New Pentesting Distribution to Compete with Kali Linux
SnoopGod is now available for your testing needs
-
Juno Computers Launches Another Linux Laptop
If you're looking for a powerhouse laptop that runs Ubuntu, the Juno Computers Neptune 17 v6 should be on your radar.