Fighting dictionary attacks with Sshutout and Fail2ban
Protection against DoS
SSH has two jails: the one just mentioned and sshd-ddos. This jail is not designed to prevent attempts to guess passwords, but to counter denial-of-service (DoS) attacks that open connections to the SSH daemon without entering a password.The logfile contains messages like this in case of a DoS attack:
sshd: Did not receive identification string from 10.0.0.150
Although you could configure multiple regular expressions per jail, many admins will prefer to assign different ban times for distributed DoS (DDoS) attacks as opposed to failed login attempts. That is, splitting this into the SSH and sshd-ddos categories makes a lot of sense.
The SSH jail is the only one set to enabled = true by default; all other jails – including sshd-ddos – have to be enabled manually.
Protection Scheme
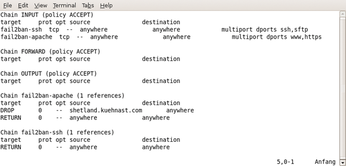
If a user enters the wrong password multiple times, the results are similar to the Sshutout results: An iptables rule is triggered and locks out all connections from the offending computer for the next five minutes (Figure 2).
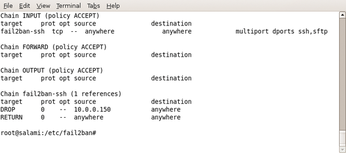 Figure 2: Fail2ban locks out a client attempting to establish a connection after a predefined number of invalid connection attempts.
Figure 2: Fail2ban locks out a client attempting to establish a connection after a predefined number of invalid connection attempts.
Protection for other services follows the same pattern (Figure 3). If you have a number of login-protected web pages on your Apache web server, Fail2ban will give you a jail to match,
[apache] enabled = false port = http,https filter = apache-auth logpath = /var/log/apache*/*access.log maxretry = 3
which you need to modify slightly. The Apache version that I run writes error messages to a separate error.log file, and not to access.log. After setting enabled = true, you can enable the jail.
Tip: A more elegant approach than simply restarting the Fail2ban daemon, which could mean disabling active iptables rules, is to send the following command from the Fail2ban client to the server:
fail2ban-client start apache
This command tells the server to add the [apache] entry to the list of active jails. To try this out, I entered a number of invalid passwords, and a new iptables rule was activated.
Infos
- Sshutout: http://www.techfinesse.com/sshutout/sshutout.html
- Fail2ban: http://www.fail2ban.org
« Previous 1 2
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.
-
New Pentesting Distribution to Compete with Kali Linux
SnoopGod is now available for your testing needs
-
Juno Computers Launches Another Linux Laptop
If you're looking for a powerhouse laptop that runs Ubuntu, the Juno Computers Neptune 17 v6 should be on your radar.