25th Chaos Communication Congress
Opening Black Boxes
One trend you couldn't fail to notice was the inroads that hackers have made into hardware black boxes. Collien Mulliner, from Fraunhofer SIT, demonstrated telephone vulnerabilities, investigating buffer overflows in Symbian OS in the process.
Harald Welte took this a step further in his guide to dismantling smartphones. More and more high-end mobile devices have two controllers: an Application Processor (AP) that handles application control, and a Baseband Processor (BP) that handles wireless activity and phone calls.
Dismantling Phones
Despite increasing numbers of SDKs for the AP – or for higher-level layers, such as Google Android – manufacturers are still reticent when it comes to hardware, which is all the more reason for Welte & Co. to investigate the hardware more closely. Many telephones have debugging soldering points for the JTAG interface on their PCBs. With more than a little dexterity and a trusty soldering iron, hackers can attach and fire up a serial console (Figure 5).
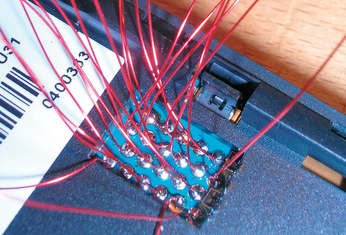 Figure 5: Wire and more than a little dexterity are needed to solder a serial console onto a Glofiish smartphone. JTAG connectors provide access.
Figure 5: Wire and more than a little dexterity are needed to solder a serial console onto a Glofiish smartphone. JTAG connectors provide access.
Genuine Vulnerabilities
Whereas the first days of the congress were colorful and entertaining, but lacking in novelties, the organizers pulled a security ace out of their sleeves on the final day. After all, data tourists used to visit Berlin to marvel over the latest vulnerabilities. An international team of researchers and hackers disclosed how they had exploited a known, but widely ignored, MD5 vulnerability, with a couple of hundred dollars, and 200 PlayStations to create a CA keypair that was indistinguishable from the real thing.
There was no answer to the question of whether investigation authorities have purchased CA certificates yet to comply with the BKA (Germany's Federal Criminal Police Office) rules introduced at the beginning of 2009. At the end of the event, our verdict was mixed – overfilled rooms, a variety of topics, and an audience that was wide awake but still slightly puzzled as to whether it was currently witnessing the sell-out of freedom on the network.
Infos
- 25c3 website with lecture notes: http://events.ccc.de/congress/2008/
- C-Base: http://www.c-base.org
- OpenPattern: http://openpattern.org
- Faifa: https://dev.open-plc.org
« Previous 1 2
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.
-
New Pentesting Distribution to Compete with Kali Linux
SnoopGod is now available for your testing needs
-
Juno Computers Launches Another Linux Laptop
If you're looking for a powerhouse laptop that runs Ubuntu, the Juno Computers Neptune 17 v6 should be on your radar.
-
ZorinOS 17.1 Released, Includes Improved Windows App Support
If you need or desire to run Windows applications on Linux, there's one distribution intent on making that easier for you and its new release further improves that feature.

