Visualize your network with Skydive
Collecting Flows
Up to this point, Skydive has not done too much. The colorful topology graph offers a neat overview of the network environment, but it does not really help with problems.
If connections between end devices cannot be established, the network is always the first suspect. Networkers need to immediately find the glitch and solve the problem. This challenge becomes even more complex when the devices involved belong to different teams. Skydive can help, recording traffic flows on the suspicious hosts and listing them in the analyzer. Select the icon of an affected network adapter in the graphical web view and launch the Packet Capture function in the right pane. Just like with Wireshark and Tcpdump, a capture filter can pick out targeted packets that are relevant to the investigation.
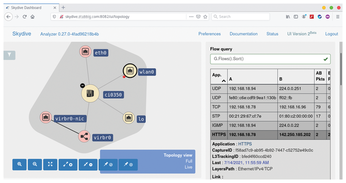
Without anyone noticing, the agent collects the flow information of the desired network adapter and sends it to its higher-level controller, which dumps the information in the Elasticsearch database. A look at the Flows column of the analyzer provides the list of all inspected IP connections (Figure 2). The dataset can be sorted or filtered as desired using the flow query. If the flow you are looking for does not appear in the table, the connection request did not reach that host, and the cause of the error must be closer to the source.
Injecting Packets
Viewing the flow information provides passive insights that do not change the network traffic. The second main task of Skydive is different: forming new packets and injecting them into the network via any agent. In this way, you can check if the test packet arrives at the intended destination.
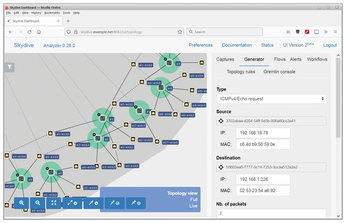
Assembling a new packet is a convenient point-and-click procedure in Skydive analyzer. In Figure 3, the generated packet simulates a ping between two terminals. Do not type in the required source and destination addresses manually; simply click on the respective network icon in the topology view.
In addition to ICMP, the web UI also supports UDP and TCP packets, in the IPv4 and IPv6 flavors. Skydive does not offer other headers (such as IPsec) or complex constructs. For a penetration test, this would be a poor harvest, but for troubleshooting, these options are quite sufficient.
Speaking of addresses: The Skydive agent sends the packet in exactly the way the analyzer tells it to. If the communication between the two endpoints goes through a default gateway, the destination MAC address in the web interface should be that of the gateway, not the destination system. This quirk does not emanate from Skydive but from the Ethernet protocol.
Once the packet starts its journey, it can no longer be distinguished from a normal packet by the switches and routers it passes through, thus helping with neutral troubleshooting.
Extending the Topology
Admittedly, the Skydive agent will not run on any old device. But zero-access switches and Windows servers will still find a place in the Skydive interface because the topology can be extended to remove the blind spots.
If there is a connection between Server A and Server B that Skydive has not detected, then the Topology rules menu item comes into play. Topology distinguishes between nodes and edges. The terms originate from graph theory and refer to the nodes of a graph and its edges as connecting lines between the nodes. Skydive uses the term node not only for the network nodes, but also for their components. For example, the server node has an edge to the eth0 node, which denotes the server's own network adapter.
A new node needs a name and a type in Skydive. In this case, an unassigned icon appears in the topology view to represent the new node. A new edge needs the identifiers of the two nodes it will connect. Just as with packet capture, the planned endpoints of the edge can be selected by clicking. In addition, each edge needs a user-definable type, such as Layer 2 for an Ethernet connection.
Skydive places no limits on the connections. The edge of eth0 does not need to lead to another network adapter but can also terminate at a block device. Skydive's flexible topology thus provides a basis for documentation and visualization. The command line is better suited for mass extensions, as described in the next section.
« Previous 1 2 3 4 Next »
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.
-
New Pentesting Distribution to Compete with Kali Linux
SnoopGod is now available for your testing needs
-
Juno Computers Launches Another Linux Laptop
If you're looking for a powerhouse laptop that runs Ubuntu, the Juno Computers Neptune 17 v6 should be on your radar.
-
ZorinOS 17.1 Released, Includes Improved Windows App Support
If you need or desire to run Windows applications on Linux, there's one distribution intent on making that easier for you and its new release further improves that feature.