Encrypting and transferring system email with Zeyple
Key Service

IT specialists often rely on automatic notification for status messages and logfiles by email. A Python script named Zeyple uses GPG to protect potentially sensitive messages against unauthorized viewing.
Whether you choose Logdigest [1], LogSurfer [2], your own script, or cron [3], email is a common choice for quickly updating admins about the state of the system.
The information contained in system update messages is not just informative, it's also frequently sensitive, containing details such as usernames, email addresses, and even data that is subject to data protection legislation (Figure 1).
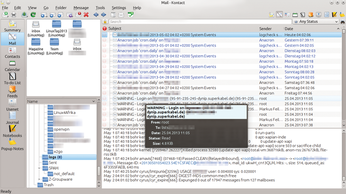 Figure 1: Email addresses, login information, and more: Many messages to sys admins include vulnerable data that easily can be sniffed through a man-in-the-middle attack.
Figure 1: Email addresses, login information, and more: Many messages to sys admins include vulnerable data that easily can be sniffed through a man-in-the-middle attack.
If you send these kinds of messages unencrypted, you could be providing important clues to attackers and making it easier for surveillance agencies to monitor your activities. Securing transport with SSL/TLS is one approach to adding security. However, this method does not provide complete protection for mail content.
Once a message reaches the provider's mail transfer agent (MTA) at the other end, encryption stops, and the mail is back in cleartext. Therefore, to make email communication completely inaccessible to outsiders requires continuous encryption of the content from the sender to the receiver. Linux systems offer a relatively easy-to-use encryption method called GPG, which stands for GNU Privacy Guard. This approach, which works well for routine communications, requires a bit more preparation on a server that you want to encrypt and send without user interaction.
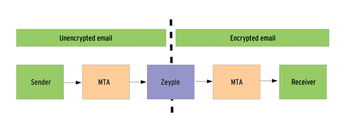
The most elegant method passes email from the MTA queue to a program that encrypts the messages and then puts them back in the queue. Then, the MTA routes the mail as usual to the receiver or receivers (Figure 2). This process is exactly what the Python script Zeyple [4], by Cédric Félizard, does. The tool, named Zeyple Encrypts Your Precious Log Email, a recursive acronym in the best Unix/Linux style, hooks into the MTA queue where it encrypts all email to recipients whose public GPG keys are on record.
Postfix Example
Using Postfix as an example, I'll show you how to install Zeyple and configure the SMTP server to cooperate with it. Zeyple is available for download on GitHub [4] and should also work with other MTAs that provide an appropriate queue filter mechanism, according to the developers.
The install.sh script in Listing 1 sets up cooperation between Zeyple and Postfix [5]. The example is based on Debian Squeeze with Postfix version 2.7.2, but with minor adjustments, it should work just as well on other distributions. For encryption to work, the system administrator needs to generate a GPG key pair and upload the public key to a keyserver.
Listing 1
install.sh
Installation Script
Lines 5 and 7 of the listing define the internal (e.g., root@<local.domain>) and the external (e.g., admin@example.com) email addresses. Then, you need to choose an appropriate keyserver on which to store the public key for the external email addresses and add its URL to line 9.
Dependencies
For the installation script to work, Zeyple also needs the packages sudo, GPG, and python-gpgme (line 12). GPG is usually already installed on Debian squeeze, but not sudo or python-gpgme. Line 15 creates the user zeyple, under whose privileges the script runs. Under no circumstances should the admin run Zeyple with the privileges of the postfix or root accounts.
Line 20 loads the configuration example from GitHub, and the script creates the configuration directory and the directory for the GPG key database for Zeyple before setting up permissions.
Line 29 transports the sample configuration to /etc/zeyple, which you can use without any changes. The next few lines move the Python script zeyple to /usr/local/bin and make it executable.
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
So Long Neofetch and Thanks for the Info
Today is a day that every Linux user who enjoys bragging about their system(s) will mourn, as Neofetch has come to an end.
-
Ubuntu 24.04 Comes with a “Flaw"
If you're thinking you might want to upgrade from your current Ubuntu release to the latest, there's something you might want to consider before doing so.
-
Canonical Releases Ubuntu 24.04
After a brief pause because of the XZ vulnerability, Ubuntu 24.04 is now available for install.
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.