Manage Internet uploads with Portmaster
State-of-Art
Open the graphical front end, and you are welcomed by a state-of-art interface divided into four areas. On the far left, the program offers a vertical buttonbar at the edge of the window, which you can use to configure the application modules.
To the right is a column with the Network Rating. This is where you specify how restrictive Portmaster is – the Trusted option is the default. When the Untrusted and Danger options are selected, the tool applies more restrictive filters. In addition, the application displays status and event messages in this column.
The rightmost Network Monitor column lists the individual connections from the computer to the Internet. The largest column on the far right of the program window shows the details for each connection. Clicking on the desired application lets you display detailed information. The window then opens a list view with more detailed information about the individual connections (Figure 3).
Beyond the plain-vanilla status and connection display, the Portmaster interface gives users the option of editing individual connections. To do so, click on the desired application in the overview and then on the corresponding entry in the Connection History. Portmaster then displays all connections in the form of a table.
Use the Add Rule button to make further settings by defining new rules. In the subsequent dialog, you can enable or disable existing filter lists. Users with a little more networking knowledge can add their own custom rules using iptables syntax. Portmaster lets you define which data packets will pass through or be blocked (Figure 4).
You can set individual rules for all applications with Internet access, regardless of whether the application is currently running. Portmaster automatically detects all applications with network access and displays them in a list. Access this list by clicking the second button from the top on the far left of the vertical buttonbar. All apps then appear on the right, with Portmaster distinguishing between active and inactive applications (Figure 5).
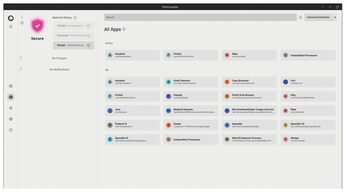 Figure 5: Even at the level of the individual programs, you can manage who the apps are allowed to send data to.
Figure 5: Even at the level of the individual programs, you can manage who the apps are allowed to send data to.
Settings
To modify the global settings for Portmaster, click on the gear icon in the vertical buttonbar. The Global Settings dialog pops up on the right of the window, and you can use the convenient sliders to configure settings sorted into three connection categories.
For example, you can ignore DNS servers operating in your own intranet in larger environments, although Portmaster by default does not use them for name resolution until you reach the Untrusted level. You can also extend this setting to the Trusted level, network access via a secure intranet, using the slider.
SPN
Portmaster provides tunneled access to the Internet using the SPN. This network is an alternative to traditional VPN services, but it has an added technical feature. The SPN doesn't just route data packets through a tunnel between client and server; it also uses an onion structure similar to the TOR network, with the packets passing through multiple servers.
The SPN is currently still in the alpha phase, which is why Portmaster disables the service by default. Like public VPN services, the SPN requires separate access. The developers offer a simple, commercial subscription model, with an unlimited transfer quota for up to five devices at EUR9.90 (~$10) per month or EUR99 (~$103) per year.
To activate the SPN network, just click on the second button from the bottom in the vertical buttonbar on the left. A login dialog with some information now appears on the right, and you can use it to switch Portmaster to SPN mode. On top of this, in the dialog below Global Settings, you also need to move the slider in the SPN group from Off to On. After doing so, all connections are established via the SPN (Figure 6).
« Previous 1 2 3 Next »
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
So Long Neofetch and Thanks for the Info
Today is a day that every Linux user who enjoys bragging about their system(s) will mourn, as Neofetch has come to an end.
-
Ubuntu 24.04 Comes with a “Flaw"
If you're thinking you might want to upgrade from your current Ubuntu release to the latest, there's something you might want to consider before doing so.
-
Canonical Releases Ubuntu 24.04
After a brief pause because of the XZ vulnerability, Ubuntu 24.04 is now available for install.
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.




