The sys admin's daily grind: Knockd
Knock-Knock
Horror stories are full of scary characters knocking on doors at night. On Linux, we just call this port knocking, and it can actually be quite useful.
If you prefer not to have an obvious administrative port for your iptables firewall – but do need a secret one – port knocking is an interesting option that can put off script-based attacks. For the ambitious but secretive admin, the tool of choice is Knockd [1].
The package includes two components: Knock is the client that sends knocking signals, which the Knockd daemon receives.
Knocking
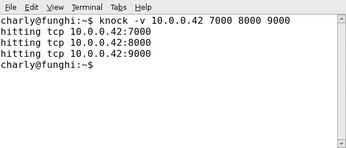
To monitor the process, Knock, the knocking client, only needs the port number on which to knock and a -v option.
For example:
knock -v 10.0.0.42 7000 8000 9000
The tool responds immediately with the command-line output shown in Figure 1.
The /etc/knockd.conf configuration file lets the system administrator specify the action the daemon performs when it receives a valid hit.
See Listing 1 for an example.
Listing 1
/etc/knockd.conf
In a production environment, choose a more unusual port number, of course.
Morse Code for Fun and Profit
If it recognizes the signal, Knockd opens up port 22 for the requesting IP, which passes in its own IP (see Figure 2).
 Figure 2: The Knockd daemon uses iptables to open up port 22 for the requesting IP, but only if it recognizes the knock signal.
Figure 2: The Knockd daemon uses iptables to open up port 22 for the requesting IP, but only if it recognizes the knock signal.
If you knock on the ports in the wrong order, the daemon will shut down SSH access. Scatterbrained admins (like me) have another option – knockd.conf, which looks like this:
start_command = /usr/sbin/iptables -A INPUTU -s %IP% -p tcp --syn --dport 22 -j ACCEPT cmd_timeout = 10 stop_command = /usr/sbin/iptables -D INPUTU -s %IP% -p tcp --syn --dport 22 -j ACCEPT
After knocking, the daemon launches start_command, then waits the number of minutes specified in cmd_timeout before executing stop_command.
Conclusion
Really paranoid system administrators will relish the option of configuring a file with a sequence of ports. Each sequence expires after use.
Infos
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
So Long Neofetch and Thanks for the Info
Today is a day that every Linux user who enjoys bragging about their system(s) will mourn, as Neofetch has come to an end.
-
Ubuntu 24.04 Comes with a “Flaw"
If you're thinking you might want to upgrade from your current Ubuntu release to the latest, there's something you might want to consider before doing so.
-
Canonical Releases Ubuntu 24.04
After a brief pause because of the XZ vulnerability, Ubuntu 24.04 is now available for install.
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.