Zero to Hero
Turbocharge Your Network with Zeroshell

© lassedesignen, Fotolia.com
Turn an old unused computer into a state-of-the-art router.
Special Thanks: This article was made possible by support from Linux Professional Institute
Zeroshell is a Linux distribution that will help you roll out useful network-related services. If you are responsible for a bunch of networked computers on a small LAN, you can use the Zeroshell distribution to transform an aging, unused computer into a multi-purpose gateway server with more services and flexibility than you can wring out of most off-the-shelf routers.
The Zeroshell Linux distribution provides various essential network services ranging from DHCP and firewall to VPN and load-balancing. It has a RADIUS server for WPA2 authentication, as well as a Captive Portal instance to create public hotspots. You can also use Zeroshell to shape network traffic, act as a HTTP Proxy Server, and even deploy a VPN. The icing on the cake is that you can do all this and a lot more from the comfort of an easy graphical interface.
Zeroshell has modest hardware requirements and works nicely even on an antiquated Celeron box with 1GB of RAM. It’s available as a Live installable ISO image as well as a USB image. Before anchoring the distribution to the computer, you can experience it in all its glory from the Live environment. In addition to x86, the project also hosts images for several ARM-based single-board computers, such as the Raspberry Pi and the Orange Pi.
Broadly speaking you can deploy Zeroshell in two ways. You can either let Zeroshell replace your existing router, or you can supplement it with Zeroshell. If used as a replacement for the existing network hardware, you’ll need to equip the Zeroshell server with two network cards, one of which will plug into the Internet modem, and the other into a network switch that connects to the other computers on the network. If the Zeroshell server only needs to serve a small number of computers, you can turn the Zeroshell machine into a wireless access point that’s connected to the existing Internet-enabled router via Ethernet. Using the two in tandem is a popular option, because you can leave the the task of doling out IP addresses to the router, which saves you the effort of configuring Zeroshell’s routing and DHCP features and allows you to focus on more interesting tasks.
Break the Shell
To get started, boot Zeroshell from either the CD or the USB image. The distro boots up to a customised text-based interface (Figure 1). Before going any further, press P to change the default password (zeroshell) for the admin user. Next up, make sure Zeroshell is on the same subnet as the rest of the network. By default Zeroshell assigns itself to the 192.168.0.x subnet. If your existing router is on the same subnet, you’re in luck. Press i and note the IP address shown at the top of the page. That’s the address of Zeroshell’s web-based interface, and it’s usually 192.168.0.75. You’ll still have to point it to your gateway, so press g and enter the IP address of your gateway server.
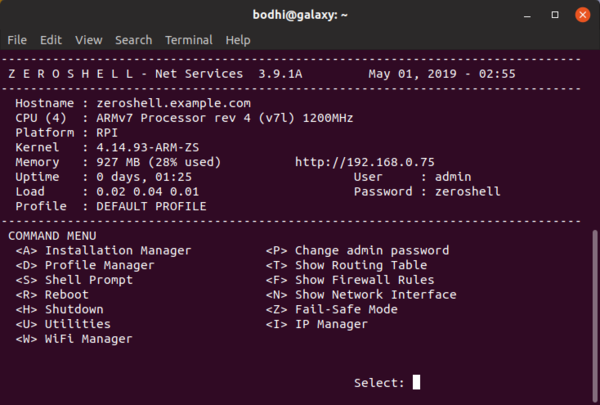 Figure 1: The Profile Manager feature helps you save different configurations under different profiles.
Figure 1: The Profile Manager feature helps you save different configurations under different profiles.
If you are on a different subnet, for instance, if your router is located at 192.168.1.1, then you’ll need to change Zeroshell’s default address and bring it on the same subnet as the rest of the network. For this, press i to bring up the IP Manager menu. Then bring down the Ethernet interface by pressing s and following the wizard. Now press d and delete the default IP address before pressing g to set the default gateway address to your existing router’s IP address. Now press a to enter a new static IP address for the Zeroshell server. To bring the changes into effect, press s to change the status of the Ethernet to up. The interface will now change to reflect the new IP addresses. Press q to return to the main menu.
You can now access Zeroshell using a web browser on any computer within the network by pointing the browser at the IP address you’ve just set. When it prompts you for login credentials, use the admin username, along with the password you defined earlier. Although the web interface (Figure 2) can handle the bulk of its configuration, you’ll occasionally need to access Zeroshell’s console interface as well. Instead of hopping over to the Zeroshell server, you can access it remotely via SSH. To enable SSH, head to the web interface and click on the SSH tab under the Setup section. In the popup window, toggle the Enabled checkbox. Then enter the subnet of your network (such as 192.168.0.1/24) in the IP address text box and click the + button. Bring the changes into effect with the Save button. You can now ssh into the Zeroshell server from any computer on the subnet with:
$ sudo ssh admin@192.168.0.75
Reroute Traffic
The next step is to configure the wireless adapter on the Zeroshell server to act as a wireless access point. Although all network cards and adapter supported by the Linux kernel should work with Zeroshell, it is still advisable to scroll through the list of hardware that’s known to work with the distribution.
To verify that the distribution can work with your wireless adapter, head to the console-based menu and press w to bring up the WiFi Manager menu. You’ll get an error if the card isn’t recognized. If everything’s good, press n to kick off a wizard that helps define the settings for the new access point. Zeroshell will prompt you for the SSID of the new access point, as well as the encryption mechanism you’d like it to use. Although the default options will work in most cases, review each carefully, especially the encryption mechanism.
Once you’re through with the wizard, your wireless access point should be visible to the devices in the vicinity. However, to hand out IP addresses to these devices and allow them to browse the Internet, you’ll need to create a bridge interface between the wireless adapter and the router that’s connected to the Ethernet card.
Log into the web-based interface and head to the Network tab under the Setup section. Then click the button labeled Gateway to make sure the default gateway is set to your router’s IP address (192.168.0.1 in our case). Close the window and click the New BRIDGE button, which pops open a window that lists both the Ethernet (eth00) and wireless adaptor (wlan00) interfaces under Available Interfaces. Select each and click the button with the three right arrows to move the selected interface into the Bridge Components list (Figure 3). Do this for both the interfaces, then click Save to activate the new bridged interface. That’s it. You can now connect devices to the new wireless access point.
 Figure 3: Make sure you only add the network interfaces you want to bridge. Ignore any others that might be listed like VPN.
Figure 3: Make sure you only add the network interfaces you want to bridge. Ignore any others that might be listed like VPN.
You can also shield the devices connected to Zeroshell’s access point from malicious code floating around on the Internet by enabling the Transparent Antivirus Proxy feature. Scroll down to the Security section in the left-hand column and click the HTTP Proxy link. Tick the Enabled box and click the Save button to bring the proxy online. This can take several minutes as Zeroshell fetches the latest antivirus definition from ClamAV’s website. The Update Log button will help you keep track of the progress.
Once the proxy is active, click the + icon in the HTTP Capturing Rules section and add two separate Capture Request rules for all traffic passing through the wireless and Ethernet adaptors. Unless your users are known to frequent the darkest corners of the Internet, you can go easy on ClamAV’s server and tune down the number of times Zeroshell checks it for new definitions and updates from the default 12 to a more reasonable value, say 2. Also, make sure you change the default mirror to one that’s closer to where you are located.
Open Sesame
Once you have the wireless access point up and running, you can configure other services, such as Captive Portal. Head to the Captive Portal link under the Users section and toggle the GW checkbox. Before you activate the service, use the Interface pulldown menu to select the WLAN00 interface and click the Save button to bring it online (Figure 4). It really is that simple. When the other devices in your network now connect to the access point you’ve created using Zeroshell, they’ll be asked to first authenticate before they are allowed to browse the web. By default, the server only has the default admin user. To add more users, click the Users link under the Users section on the left. You’ll get a list all the configured users. Use the Add link in the top bar to add more users.
 Figure 4: Switch to the Authentication tab to tweak the default template for the Captive Portal login page.
Figure 4: Switch to the Authentication tab to tweak the default template for the Captive Portal login page.
Another common network service that is quite a chore to roll out is OpenVPN. Configuring OpenVPN is quite an involved process that includes pulling in and configuring various pieces of software and generating the appropriate secure certificates. However, Zeroshell reduces the process down to a couple of steps. All you need to do to use OpenVPN is to enable the service and export the certificates to your clients.
Zeroshell supports different mechanisms for VPN authentication. You can use simple usernames and passwords, X.509 secure certificates, or both, which is what I’ll be doing. To grab the certificates, click on the Users links under the User section on the left. Select any user and click the X509 tab in the top bar. From here you can review, revoke, and generate a new certificate for the selected user (Figure 5). For the moment, though, just save the certificate. Select PEM certificate format in the pull-down menu, then click the Export button and save the admin.pem file to your local machine.
 Figure 5: Make sure you read about Zeroshell's excellent skills for issuing and managing X509 certificates (https://zeroshell.org/x509-details/).
Figure 5: Make sure you read about Zeroshell's excellent skills for issuing and managing X509 certificates (https://zeroshell.org/x509-details/).
Now grab the certificate for the Trusted Certificate Authority, which, in our case, is the Zeroshell server itself. Scroll down to the Security section in the left-hand column and click the X.509 CA link. Switch to the Trusted CAs tab in the top bar, which pops open a window with a list of trusted CAs. Select the only listed entry for the local Zeroshell server, and click the Export button to save the TrustedCA.pem file. Finally, click the VPN link under the Network section in the left-hand column and toggle the Enabled checkbox. Finally, use the Save button to apply the settings and bring the server online. That’s all there is to it. Now follow the detailed instructions on the Zeroshell website to configure your Linux, Windows, and OS X clients to connect to the Zeroshell OpenVPN server.
This is by no means an exhaustive guide on Zeroshell, but this article should give you a taste of Zeroshell’s simplicity and networking prowess. In addition to the built-in functions, you can get more services via add-ons. To include add-ons, you’ll need to activate Zeroshell’s special repository, either via a small donation or by various other means to help spread the word about the project.
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
So Long Neofetch and Thanks for the Info
Today is a day that every Linux user who enjoys bragging about their system(s) will mourn, as Neofetch has come to an end.
-
Ubuntu 24.04 Comes with a “Flaw"
If you're thinking you might want to upgrade from your current Ubuntu release to the latest, there's something you might want to consider before doing so.
-
Canonical Releases Ubuntu 24.04
After a brief pause because of the XZ vulnerability, Ubuntu 24.04 is now available for install.
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.


