Brad Spengler Exposes Exploit in Linux Kernel 2.6.31
The developer behind the grsecurity.net security portal, Brad Spengler, has released videos on the Web that demonstrate a security hole in the current Linux kernel.
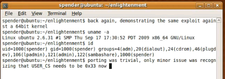
Brad Spengler (alias Spender) is a known entity in the Linux security field. Revealing his videos on his YouTube channel certainly lends his case credibility. The videos show that the exploit uses a buffer overflow in the perf_counter after a kernel crash, which also bypasses SE Linux.
A recent followup to Spengler's video for a 32-bit system is one for a 64-bit Ubuntu exploit. He intends to publish details soon. Fortunately the exploit is currently not freely circulating.
Comments
comments powered by DisqusSubscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
System76 Releases COSMIC Alpha 7
With scores of bug fixes and a really cool workspaces feature, COSMIC is looking to soon migrate from alpha to beta.
-
OpenMandriva Lx 6.0 Available for Installation
The latest release of OpenMandriva has arrived with a new kernel, an updated Plasma desktop, and a server edition.
-
TrueNAS 25.04 Arrives with Thousands of Changes
One of the most popular Linux-based NAS solutions has rolled out the latest edition, based on Ubuntu 25.04.
-
Fedora 42 Available with Two New Spins
The latest release from the Fedora Project includes the usual updates, a new kernel, an official KDE Plasma spin, and a new System76 spin.
-
So Long, ArcoLinux
The ArcoLinux distribution is the latest Linux distribution to shut down.
-
What Open Source Pros Look for in a Job Role
Learn what professionals in technical and non-technical roles say is most important when seeking a new position.
-
Asahi Linux Runs into Issues with M4 Support
Due to Apple Silicon changes, the Asahi Linux project is at odds with adding support for the M4 chips.
-
Plasma 6.3.4 Now Available
Although not a major release, Plasma 6.3.4 does fix some bugs and offer a subtle change for the Plasma sidebar.
-
Linux Kernel 6.15 First Release Candidate Now Available
Linux Torvalds has announced that the release candidate for the final release of the Linux 6.15 series is now available.
-
Akamai Will Host kernel.org
The organization dedicated to cloud-based solutions has agreed to host kernel.org to deliver long-term stability for the development team.

How to mitigate such risks..
At our IT Security Conference, AthCon, www.athcon.org which will be hosted in Athens, Greece in Q2 2010, we'll be discussing how to mitigate such vulnerabilities in production code & how to thwart null pointer dereference vulnerabilities once & forever.
- AthCon team.