Korset: Linux security thanks to static analysis
Coworkers at the University of Tel Aviv have presented a prototype for a new host-based intrusion detection system (HIDS) for Linux. Named Korset, it uses static code analysis and promises zero failures.
A host-based intrusion system (HIDS) models an application’s behavior and if the behavior deviates from the model, it sends an alarm. Earlier methods of intrusion detection depended either on static data derived from machine learning or on program policies created by developers. In the views of Professor Avishai Wool and kernel developer Ohad Ben-Cohen, the first method is susceptible to false positives and the second one costly.
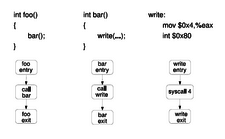
Instead, Wool and Ben-Cohen use a behavioral model automated through static analysis of source code and object files resulting in control flow graphs (CFGs). Since most attacks are accompanied by system calls, the CFGs limit themselves to these calls and document the legitimate pattern for each application. If a program deviates from the pattern, the kernel ends the process.
Korset consists of two parts: a static analyzer in user space and a runtime monitoring agent in the kernel. The analyzer is drawn into the program’s build process and creates a CFG for each executable, object data and library. The Korset runtime monitor is built into the kernel. Once a detected program runs, the agent monitors any resulting system calls and compares them with those of the CFG model.
Wool’s and Ben-Cohen’s report to the Ottawa Linux Symposium 2008 (PDF) includes further details about their work, as does their presentation at the Black Hat US 2008 conference.
A Korset prototype download is available under GPLv3 terms. The developers designate the implementation as pre-alpha software not yet ready for use, but proof-of-concept.
Comments
comments powered by DisqusSubscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
The Next Linux Kernel Turns 7.0
Linus Torvalds has announced that after Linux kernel 6.19, we'll finally reach the 7.0 iteration stage.
-
Linux From Scratch Drops SysVinit Support
LFS will no longer support SysVinit.
-
LibreOffice 26.2 Now Available
With new features, improvements, and bug fixes, LibreOffice 26.2 delivers a modern, polished office suite without compromise.
-
Linux Kernel Project Releases Project Continuity Document
What happens to Linux when there's no Linus? It's a question many of us have asked over the years, and it seems it's also on the minds of the Linux kernel project.
-
Mecha Systems Introduces Linux Handheld
Mecha Systems has revealed its Mecha Comet, a new handheld computer powered by – you guessed it – Linux.
-
MX Linux 25.1 Features Dual Init System ISO
The latest release of MX Linux caters to lovers of two different init systems and even offers instructions on how to transition.
-
Photoshop on Linux?
A developer has patched Wine so that it'll run specific versions of Photoshop that depend on Adobe Creative Cloud.
-
Linux Mint 22.3 Now Available with New Tools
Linux Mint 22.3 has been released with a pair of new tools for system admins and some pretty cool new features.
-
New Linux Malware Targets Cloud-Based Linux Installations
VoidLink, a new Linux malware, should be of real concern because of its stealth and customization.
-
Say Goodbye to Middle-Mouse Paste
Both Gnome and Firefox have proposed getting rid of a long-time favorite Linux feature.

Won't protect apps that include an interpreter.
Now, if Korset could analyze the script itself, not the interpreter, then you might get more information. But languages like Python and Ruby are so dynamic that static analysis can't usually tell you much, unless you restrict the language.
Not all that useful