The Ratproxy security scanner looks for vulnerabilities in web applications
Rat Catcher

© Illustrations on this page: Anna Telnova, Fotolia
Google's Ratproxy is a free testing tool that searches for security problems in web applications.
Several test suites help you look for vulnerabilities in web-based applications [1] [2], but many of these applications are expensive or difficult to use. Wouldn't it be nice just to press a button to find out what vulnerabilities exist in your own software – along with a line reference to help you find the problems in the source code?
Ratproxy [1] is a tiny but powerful tool with a simple approach to searching for problems in web applications. The Ratproxy security testing tool originated in the development labs Google, where it was created to test Google's own applications. In July 2008, the company decided to release the current version to the general public under the Apache License 2.0.
Google describes Ratproxy as a "semi-automatic, largely passive web application security audit tool." Lurking behind this cryptic description is a tool with a simple purpose: Ratproxy sniffs communications between the browser and the application, logging the data stream and checking the log for known issues, risks, and vulnerabilities. Developers can launch Ratproxy and watch the output. Ratproxy reaches places that competitive products find difficult to access. For example, other tools might find it hard to reach password-protected areas, or they could stumble over some forwarding scenarios. In the same way, Ratproxy cleverly works around Javascript issues. Legacy test tools employ guess work to discover which function will be used next. This problem occurs particularly in GUI testing, wherein users typically have a choice of various buttons and menus. Ratproxy, on the other hand, simply waits to see what the user does next in the browser.
Because Ratproxy does not cause a noticeable increase in network traffic, it even lets you check applications that are deployed in production environments. (Other scanners launch DOS or cross-site scripting attacks that are likely to bring a production system to its knees.)
Setting the Mousetrap
Deploying Ratproxy is simple: Just download the source code from the homepage and run make to build the dozen or so source files. The tool does not require a configure script or have any major dependencies. What you do need are the libcrypto and libssl libraries (typically supplied as part of the OpenSSL distribution) and corresponding headers.
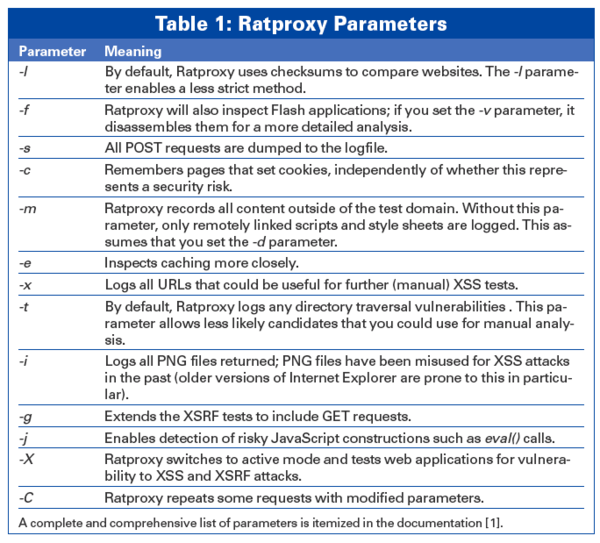
Starting the test tool is slightly more complicated: No fewer than 22 parameters (Table 1) govern the nature and scope of the tests Ratproxy performs. The parameters are also responsible for defining the level of detail to output. To avoid being plowed under in an avalanche of messages when you first launch the program, start with the default settings:
./ratproxy -v /tmp -w ratproxy.log -d mydomain.com -lfscm
This command points Ratproxy at the web application in the mydomain.com domain. Ratproxy will ignore any URLs not on this server. (This approach is a way of making sure that Ratproxy will not run off and accidentally test external ad sites.) The http traffic sniffed by Ratproxy is dumped into a multitude of tiny files in the temporary directory (-v /tmp), whereas the analysis of the results – that is, the information you are actually interested in – is stored in ratproxy.log. The Ratproxy Parameters box explains the Pandora's box of command-line options.
If you prefer a full broadside, you can change the parameters as follows:
./ratproxy -v /tmp -w ratproxy.log -d mydomain.com -lextifscgjm
The optional duo -XC (note the uppercase letter in the command name), releases Ratproxy from its passive role. Once released, Ratproxy will check to see how well your web application withstands XSS and XSRF attacks (-X), and it will repeat requests with modified parameters (-C).
If the web application returns Flash objects, Ratproxy can disassemble and analyze them. Ratproxy relies on the Flare ActionScript decompiler for this; unfortunately, Flare is only available as a prebuilt closed source application. By default, Ratproxy supports execution on x86 processors. A version for 64-bit Linux is available on the Flare homepage [4]. First you must download the file, unpack it, and store the results in flare-dist.
Shadowing the User
Ratproxy's interactive orientation has several benefits, but it is also the tool's major deficiency. If the user does not execute a function, Ratproxy does not test it. Before you launch Ratproxy, you should think carefully about which parts of the web application you want to test – and in which order.
Connected
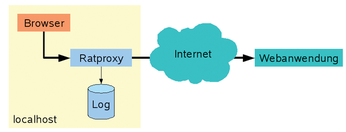
Once you see the message Accepting connections on port 8080/tcp (local only), you know that the test tool is listening on port 8080 for incoming browser requests. The next step is to set up the browser to direct all communications via Ratproxy. The easiest way of doing this is to enter this port as a proxy on your own machine (127.0.0.1 or localhost) (Figure 1).
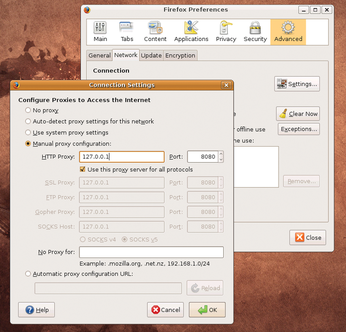 Figure 1: To point Firefox to Ratproxy, first select Edit | Settings in the main menu; select Advanced, choose the Network tab, and click on the Settings button. In the Connection Settings dialog box, enable Manual proxy configuration, and type the settings for the proxy configuration.
Figure 1: To point Firefox to Ratproxy, first select Edit | Settings in the main menu; select Advanced, choose the Network tab, and click on the Settings button. In the Connection Settings dialog box, enable Manual proxy configuration, and type the settings for the proxy configuration.
This tells the browser to forward all requests to localhost:8080, where Ratproxy will analyze the requests before passing them on to the web application (Figure 2). Because the test tool sniffs traffic passively, all of this is absolutely transparent and has only a minimal effect on execution speed. The -X and -C parameters, however, are an exception to this rule. They tell Ratproxy to switch to "disruptive mode" and actively interfere with communications. (The effects of these parameters will vary.)
If you use a genuine proxy to access the web, which is the case in many corporate environments, you need to pass the -P host:port parameter to Ratproxy, in which host and port represent the data for your proxy. This feature means you can deploy Ratproxy as part of a chain of other test tools.
Throughput
The next step is to access the web application in your browser and work in the normal way. To avoid interference from other sources, Google recommends closing all other browser windows and flushing the browser cache before you start. Ratproxy will now monitor all your actions and log them in ratproxy.log.
In the case of SSL-encrypted data, Ratproxy will replace the certificate served up by the web application with its own. A good browser will alert you to this. To carry on with the test, you must accept the new certificate. The Ratproxy documentation [1] warns against storing the certificate permanently in your browser. After all, everyone who downloads Ratproxy knows the certificate. Because Ratproxy forces a certificate on you, another problem appears: Ratproxy negotiates all further steps with the web application, so you can't be 100 percent certain that you are talking to your own server. Thus, you should avoid using critical (administrative) accounts or entering sensitive data while being monitored by the tool.
On top of this, you should resist the temptation to use wget to feed the website to Ratproxy. Most of Ratproxy's tests rely on user interaction and would simply be dropped in the case or a wget command.
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Canonical Releases Ubuntu 24.04
After a brief pause because of the XZ vulnerability, Ubuntu 24.04 is now available for install.
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.