Implementing Zero Trust Security
Aiming for Zero

Some old-school admins are still philosophizing about secure internal networks, but the experts have already moved on: Zero trust architectures use a reliable but complex strategy to protect the network from all threats – inside and outside.
In the third year of the coronavirus pandemic, it has now long been clear that many companies are likely to remember the virus as beneficial to their own business. VPN solution vendors definitely fall into this category: When home office and teleworking mutated from the exception to the rule in many companies, existing VPN solutions became substantially more in-demand. Hardly anyone expected the load on the VPN gateways to explode overnight. The large network manufacturers were happy to help out their customers as many admins purchased more powerful systems for OpenVPN (Figure 1).
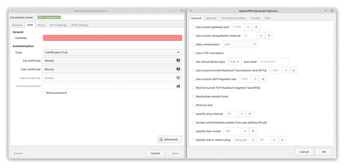 Figure 1: Homegrown VPN solutions, such as this one based on OpenVPN, are no longer suitable for state-of-art security. © KIT
Figure 1: Homegrown VPN solutions, such as this one based on OpenVPN, are no longer suitable for state-of-art security. © KIT
But do VPNs really solve the problem of network security? Many experts are not so sure. Implicitly, all parties involved with VPNs start from the following premise: There is a difference between the internal and the external network, and it is safe to treat internal clients differently from external clients. VPNs are regularly used specifically because admins do not want certain services to be accessible from the Internet at all. In many companies, VPNs form part of a security architecture that has grown organically over many years. Because security requirements have increased continuously over the past two decades, companies have invested more and more money in private networks and cut off more and more services from the outside world.
[...]
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Nitrux 6.0 Now Ready to Rock Your World
The latest iteration of the Debian-based distribution includes all kinds of newness.
-
Linux Foundation Reports that Open Source Delivers Better ROI
In a report that may surprise no one in the Linux community, the Linux Foundation found that businesses are finding a 5X return on investment with open source software.
-
Keep Android Open
Google has announced that, soon, anyone looking to develop Android apps will have to first register centrally with Google.
-
Kernel 7.0 Now in Testing
Linus Torvalds has announced the first Release Candidate (RC) for the 7.x kernel is available for those who want to test it.
-
Introducing matrixOS, an Immutable Gentoo-Based Linux Distro
It was only a matter of time before a developer decided one of the most challenging Linux distributions needed to be immutable.
-
Chaos Comes to KDE in KaOS
KaOS devs are making a major change to the distribution, and it all comes down to one system.
-
New Linux Botnet Discovered
The SSHStalker botnet uses IRC C2 to control systems via legacy Linux kernel exploits.
-
The Next Linux Kernel Turns 7.0
Linus Torvalds has announced that after Linux kernel 6.19, we'll finally reach the 7.0 iteration stage.
-
Linux From Scratch Drops SysVinit Support
LFS will no longer support SysVinit.
-
LibreOffice 26.2 Now Available
With new features, improvements, and bug fixes, LibreOffice 26.2 delivers a modern, polished office suite without compromise.
