Features
Loud and Clear
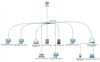
Convert data to diagrams with yEd
Build complex data structures into simple but illuminating diagrams using the yEd graph editor.
Perfect lines
Creating vector graphics using Inkscape
The Inkscape vector graphics tool replaces expensive commercial solutions such as Adobe Illustrator. This article shows how to get started with Inkscape.
On the Timeline
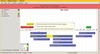
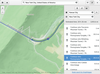
Visualize time sequences with Timeline
Timeline manages and visualizes time sequences in a simple and intuitive way.
All Systems Go
An introduction to systemd
Wondering what all the fuss is about systemd? We explain the basic concepts and capabilities of the new system management suite – coming soon to a distro near you.
Light and Shadow
Convert RAW data with LightZone
The RAW format preserves the full splendor of digital image data. You can develop this material into a format for everyday use with LightZone.
Snapshot
Back up your systems with Mondo Rescue
A timely snapshot by Mondo Rescue puts a computer back on its feet after a system failure in just a few minutes.
Great Expectations
Fedora 22 released almost on time
Fedora 22 was released a week late, but it is seriously impressive with Gnome 3.16 and the new DNF package manager. Only the installer, Anaconda, might cause beginners a headache.
Pixelized
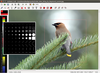
mtPaint makes painting easy
You can create pixel art in just a few mouse clicks with the paint program mtPaint, and it can even teach your works of art how to walk.
Get Back
Git-based backups with Kup
KDE's Kup tool uses Rsync and techniques from the Git version control environment for sophisticated backup with an easy GUI interface.
Orderly Situation
Simple backup with Back In Time
Despite the importance of backups, many users still view the process as too complicated and too inconvenient. Back In Time makes the unloved backup less terrifying.
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
New Linux Botnet Discovered
The SSHStalker botnet uses IRC C2 to control systems via legacy Linux kernel exploits.
-
The Next Linux Kernel Turns 7.0
Linus Torvalds has announced that after Linux kernel 6.19, we'll finally reach the 7.0 iteration stage.
-
Linux From Scratch Drops SysVinit Support
LFS will no longer support SysVinit.
-
LibreOffice 26.2 Now Available
With new features, improvements, and bug fixes, LibreOffice 26.2 delivers a modern, polished office suite without compromise.
-
Linux Kernel Project Releases Project Continuity Document
What happens to Linux when there's no Linus? It's a question many of us have asked over the years, and it seems it's also on the minds of the Linux kernel project.
-
Mecha Systems Introduces Linux Handheld
Mecha Systems has revealed its Mecha Comet, a new handheld computer powered by – you guessed it – Linux.
-
MX Linux 25.1 Features Dual Init System ISO
The latest release of MX Linux caters to lovers of two different init systems and even offers instructions on how to transition.
-
Photoshop on Linux?
A developer has patched Wine so that it'll run specific versions of Photoshop that depend on Adobe Creative Cloud.
-
Linux Mint 22.3 Now Available with New Tools
Linux Mint 22.3 has been released with a pair of new tools for system admins and some pretty cool new features.
-
New Linux Malware Targets Cloud-Based Linux Installations
VoidLink, a new Linux malware, should be of real concern because of its stealth and customization.