Secrets of a botnet developer
Web Workers

Botnets aren't all bad. We'll show you how to harness the power of the botnet architecture to solve real-world problems in a business context.
A few years ago, I developed a commercial botnet, also known as a sniper. This sniper botnet automatically purchased vehicles from a website. It also arranged for payment and scheduled shipping to my client, a very reputable automotive dealership. Although the first live test was unsuccessful, I quickly found the problem and composed an email to indicate that we were ready to try again. The email read something like this…
Dear Client, The snipers are in place and they're going to fire at cars today, starting at noon. Hopefully they'll hit something today …!
Just before I sent the message, I recalled talk of government interception and screening of email [1] [2]. I wisely reworded the message with less inflammatory language. Such is my life as a botnet developer.
Colorful language is just one of the obstacles botnet developers face, but beyond their bad reputation and unfortunate name, commercial botnets create true opportunities for business people and developers. In this article, I describe my automobile purchasing project, explore the importance of commercial botnets, and detail how open source tools, including Linux, are important in the world of botnet development and hosting.
Bad Reputation
Please don't paint the wrong picture of me when I say that I am a botnet developer. I am, in fact, an upstanding and well-published member of the IT community, with a background in security. I am also someone who develops software that delivers demonstrable value to clients. The primary way I generate that value is by automating online tasks. Examples of tasks I automate include verifying online prices, checking websites for accuracy, verifying identities, or procuring items for resale. I've even done work for a foreign government. Over 15 years and numerous projects, I have found the best way to automate online tasks is by distributing the load with a botnet.
No matter how well my botnets are received, I constantly battle the bad reputation of other people's botnets. When most people hear the word "botnet," they visualize stealthy viruses and spyware executing on compromised computers. Most of this reputation is well deserved. For example, according to a Microsoft security report published earlier this year [3], a single botnet, Conficker, infected an estimated 7 million computers worldwide. File-sharing websites were the primary carrier for the infection. The symptoms included disabled security services. The prognosis for infected computers wasn't good. If left untreated, the Conficker virus could eventually take full control of the infected computer, making it a zombie slave to a master server somewhere in the cloud. Once infected, the computers could be used for a variety of nefarious purposes, such as launching DDoS (Distributed Denial of Service) attacks or committing identity fraud.
Although the intent and distribution methods are different, the Conficker botnet shares many similarities to the "White Hat" botnets I write for commercial purposes, but the distinction is important. Not every botnet is something that should be removed by anti-virus software. In reality, a small percentage of botnets are actually quite legitimate and useful, especially to a business that is looking for a competitive advantage.
The Sniper Botnet
Although I have developed many commercial botnets, the sniper project is a particularly nice example. Unlike the nasty Conficker, this bot had no ill intent, and it was possibly the only way to solve a real business problem. Now, for the first time, I've been granted permission to talk about the project.
One day, an automotive client called with a problem. He explained that auto dealers used a special secured website to purchase returned rental vehicles (or for readers in the UK, retired cars for hire). These cars were high-value vehicles for automotive dealerships because they had low mileage and were late-model versions of a popular brand. Every automotive dealership in The United States wanted vehicles like these in their resale inventory, and everyday, several hundred of these vehicles were added to the website. Of those offered for sale, about a half-a-dozen vehicles always piqued the interest of nearly every automotive dealership in the country. These vehicles were particularly popular because they had special equipment, were discounted, or were a favorite model.
My client's problem was that, although he could view the cars for sale on the website, he wasn't able to purchase vehicles until a specific time, and when that time arrived, the servers got so much traffic from competing dealerships that it was difficult to even make a bid, let alone purchase anything. My client had discovered a great source for desirable used cars but was unable to purchase any of them. He had a business problem in need of a solution and asked for my help. I suspected that a custom botnet could solve his problem.
How Commercial Botnets Work
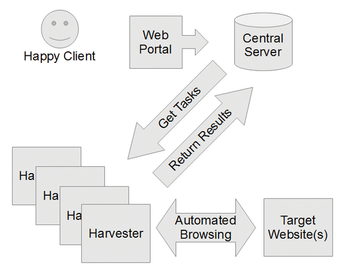
Botnets like the auto sniper share three common parts:
- A central server.
- A number of client machines (which I refer to as harvesters).
- A web portal for administering the botnet.
Figure 1 shows how these elements are interrelated.
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
New Linux Botnet Discovered
The SSHStalker botnet uses IRC C2 to control systems via legacy Linux kernel exploits.
-
The Next Linux Kernel Turns 7.0
Linus Torvalds has announced that after Linux kernel 6.19, we'll finally reach the 7.0 iteration stage.
-
Linux From Scratch Drops SysVinit Support
LFS will no longer support SysVinit.
-
LibreOffice 26.2 Now Available
With new features, improvements, and bug fixes, LibreOffice 26.2 delivers a modern, polished office suite without compromise.
-
Linux Kernel Project Releases Project Continuity Document
What happens to Linux when there's no Linus? It's a question many of us have asked over the years, and it seems it's also on the minds of the Linux kernel project.
-
Mecha Systems Introduces Linux Handheld
Mecha Systems has revealed its Mecha Comet, a new handheld computer powered by – you guessed it – Linux.
-
MX Linux 25.1 Features Dual Init System ISO
The latest release of MX Linux caters to lovers of two different init systems and even offers instructions on how to transition.
-
Photoshop on Linux?
A developer has patched Wine so that it'll run specific versions of Photoshop that depend on Adobe Creative Cloud.
-
Linux Mint 22.3 Now Available with New Tools
Linux Mint 22.3 has been released with a pair of new tools for system admins and some pretty cool new features.
-
New Linux Malware Targets Cloud-Based Linux Installations
VoidLink, a new Linux malware, should be of real concern because of its stealth and customization.