Serving false signatures to attack scanners with Portspoof
Seasoned attackers, and even some amateur cyber-vandals, find sport in trying to scan servers and hijack them at the same time (Figure 1). Firewalls and Intrusion Detection/Prevention systems can help, but if a single tool could truly stop all potential attacks, the Internet intrusion industry wouldn't even exist.
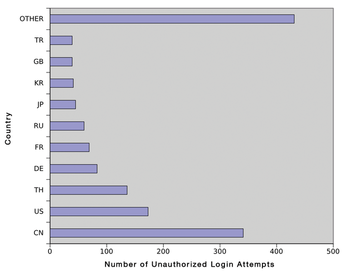 Figure 1: Number of unuathorized login attempts on the author's network in a two-month period (by country or origin).
Figure 1: Number of unuathorized login attempts on the author's network in a two-month period (by country or origin).
A professional intrusion attempt is typically preceded by reconnaissance and scanning. Many attackers simply perform a scan, which is easily automated with tools like Nmap. An attacker who discovers a firewall and similar defensive system can often guess which ports and services are worth attacking. However, a tool called Portspoof [1] intervenes to cause complications and confusion for the attacker. Portspoof answers port requests with a wild mix of signatures and payloads. This confusing and unwanted information slows down any attempted port scan, forcing the attacker to manually evaluate the results in a time-consuming process.
[...]
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Parrot OS Switches to KDE Plasma Desktop
Yet another distro is making the move to the KDE Plasma desktop.
-
TUXEDO Announces Gemini 17
TUXEDO Computers has released the fourth generation of its Gemini laptop with plenty of updates.
-
Two New Distros Adopt Enlightenment
MX Moksha and AV Linux 25 join ranks with Bodhi Linux and embrace the Enlightenment desktop.
-
Solus Linux 4.8 Removes Python 2
Solus Linux 4.8 has been released with the latest Linux kernel, updated desktops, and a key removal.
-
Zorin OS 18 Hits over a Million Downloads
If you doubt Linux isn't gaining popularity, you only have to look at Zorin OS's download numbers.
-
TUXEDO Computers Scraps Snapdragon X1E-Based Laptop
Due to issues with a Snapdragon CPU, TUXEDO Computers has cancelled its plans to release a laptop based on this elite hardware.
-
Debian Unleashes Debian Libre Live
Debian Libre Live keeps your machine free of proprietary software.
-
Valve Announces Pending Release of Steam Machine
Shout it to the heavens: Steam Machine, powered by Linux, is set to arrive in 2026.
-
Happy Birthday, ADMIN Magazine!
ADMIN is celebrating its 15th anniversary with issue #90.
-
Another Linux Malware Discovered
Russian hackers use Hyper-V to hide malware within Linux virtual machines.

