Features
Get Info, Stat
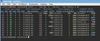
Stat-like command-line tools for admins
ASCII tools can be life savers when they provide the only access you have to a misbehaving server. However, once you're on the node what do you do? In this article, we look at stat-like tools: vmstat, dstat, and mpstat.
Bumpy Start
Exploring Red Hat Satellite Server 6
Red Hat's Satellite system management solution provides an amazing range of capabilities, but it isn't quite ready for orbit.
Lifebuoy
Restoring optical media with Dvdisaster
Even optical storage media are subject to wear. Dvdisaster helps you prevent data loss due to defective CDs, DVDs, or Blu-ray discs with a manageable amount of effort.
Misconceptions
Of lakes and sparks – How Hadoop 2 got it right
Hadoop version 2 has transitioned from an application to a Big Data platform. Reports of its demise are premature at best.
Switcheroo
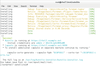
Manipulating network data streams with Netsed
Netsed is a small communication tool that lets users modify the content of TCP and UDP data packets on the local network.
Guardian Angel
Detecting vulnerabilities in the WLAN with Wifislax
Modern WiFi installations provide comfort, but they often have serious security problems. Wifislax offers an extensive collection of tools for checking the security of your wireless network.
Secret Stash
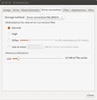
Secure your passwords and personal data with KeePassX
KeePassX is an open source personal data management tool that lets you keep your passwords, URLs, attachments, and peace of mind
News from Africa
MakuluLinux MCDE 2.0 and Xfce 7.1
Two desktop environments and two different distributions as a base – introducing MakuluLinux.
In Sync
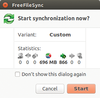
Keeping databases in sync
As your data volume grows on your home computer, you can quickly and easily create a reliable backup using FreeFileSync.
Mixed Vegetables
Photo editing with Darktable 1.6
Hardly anything affects the quality of photos more than play of light and shadow, or the brilliance of colors. Darktable fixes incorrect exposure, conceals unfavorable lighting conditions, and ensures harmonious colors.
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Nitrux 6.0 Now Ready to Rock Your World
The latest iteration of the Debian-based distribution includes all kinds of newness.
-
Linux Foundation Reports that Open Source Delivers Better ROI
In a report that may surprise no one in the Linux community, the Linux Foundation found that businesses are finding a 5X return on investment with open source software.
-
Keep Android Open
Google has announced that, soon, anyone looking to develop Android apps will have to first register centrally with Google.
-
Kernel 7.0 Now in Testing
Linus Torvalds has announced the first Release Candidate (RC) for the 7.x kernel is available for those who want to test it.
-
Introducing matrixOS, an Immutable Gentoo-Based Linux Distro
It was only a matter of time before a developer decided one of the most challenging Linux distributions needed to be immutable.
-
Chaos Comes to KDE in KaOS
KaOS devs are making a major change to the distribution, and it all comes down to one system.
-
New Linux Botnet Discovered
The SSHStalker botnet uses IRC C2 to control systems via legacy Linux kernel exploits.
-
The Next Linux Kernel Turns 7.0
Linus Torvalds has announced that after Linux kernel 6.19, we'll finally reach the 7.0 iteration stage.
-
Linux From Scratch Drops SysVinit Support
LFS will no longer support SysVinit.
-
LibreOffice 26.2 Now Available
With new features, improvements, and bug fixes, LibreOffice 26.2 delivers a modern, polished office suite without compromise.