Features
Days of Thunder
ASCII weather app for the terminal
Other applications have found less complex ways of showing the weather in a terminal, but none is as attractive as Wego.
Fine-tuned
Optimize flash memory in Linux
Solid state drives make everything run faster and more smoothly, but you can squeeze out even more performance with some practical optimization steps.
Signs of Life at the Office
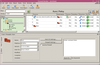
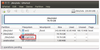
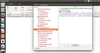
Test LibreOffice automatically
Companies that depend on LibreOffice have a reason to wonder whether the office suite is working on all systems. You can use Python and the LibreOffice API to check.
Reloaded
Automatically restore firewall filter rules
The Linux iptables packet filter lacks an easy way to load rules automatically after restarting a system, but you can automate this process several ways.
Hidden
Encryption with VeraCrypt
The VeraCrypt encryption software comes with a handy graphical interface, and the ability to hide a container in an encrypted volume adds a unique professional feature: plausibly deniable encryption.
Oh, Snap!
Restore Btrfs files at the push of a button with Snapper
Thanks to Btrfs snapshots, Snapper lets you restore a system to a previous state in case of failure.
Embedded
Storing metadata in files
With the Python XMP Toolkit, programmers can develop applications that store metadata in files.
Magic Act
Access your servers securely with a Magic URL
With a highly secure Linux server, you don't need a fixed IP address to connect over a cellphone network from anywhere on the planet if you have a Magic URL.
Steady Hand
Keep watch over your server system with Webmin
Every leading Linux distribution offers some kind of built-in GUI management tool, but the world still has room for a flexible, distribution-independent tool like Webmin.
Unleashed
Use your Chromebook with Linux
Chromebooks are firmly locked in the Google jail, but with the right know-how, you can break out of vendor lock-in and operate the devices with free software.
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Chaos Comes to KDE in KaOS
KaOS devs are making a major change to the distribution, and it all comes down to one system.
-
New Linux Botnet Discovered
The SSHStalker botnet uses IRC C2 to control systems via legacy Linux kernel exploits.
-
The Next Linux Kernel Turns 7.0
Linus Torvalds has announced that after Linux kernel 6.19, we'll finally reach the 7.0 iteration stage.
-
Linux From Scratch Drops SysVinit Support
LFS will no longer support SysVinit.
-
LibreOffice 26.2 Now Available
With new features, improvements, and bug fixes, LibreOffice 26.2 delivers a modern, polished office suite without compromise.
-
Linux Kernel Project Releases Project Continuity Document
What happens to Linux when there's no Linus? It's a question many of us have asked over the years, and it seems it's also on the minds of the Linux kernel project.
-
Mecha Systems Introduces Linux Handheld
Mecha Systems has revealed its Mecha Comet, a new handheld computer powered by – you guessed it – Linux.
-
MX Linux 25.1 Features Dual Init System ISO
The latest release of MX Linux caters to lovers of two different init systems and even offers instructions on how to transition.
-
Photoshop on Linux?
A developer has patched Wine so that it'll run specific versions of Photoshop that depend on Adobe Creative Cloud.
-
Linux Mint 22.3 Now Available with New Tools
Linux Mint 22.3 has been released with a pair of new tools for system admins and some pretty cool new features.