Testing Password Quality
Creating secure passwords and testing their quality
ByCreate secure passwords with the help of a password generator and check for quality at the same time.
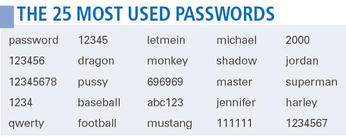
When choosing a password, your own first name is not a good choice, especially if it’s Michael or Jennifer: These names are among the 25 most often used credentials worldwide. Security specialist Mark Burnett has taken more than six million passwords and created a list ranking the most popular examples (see the “25 Most Used Passwords” box). Users especially like to use password and 123456 as passwords.
Just like the other items in the list, these passwords are fairly easy to remember – unfortunately, though, they are anything but secure, for several reasons: They are all too short, contain only lowercase letters or numbers, and use terms that can be found in any English dictionary. Because these 25 passwords are used extremely often, an invader only has to try them out one after the other. The chances of gaining access in this way are good, and no specialized cracking programs or a powerful computers are needed.
Consequently, these 25 passwords should never be used. On the other hand, it is also not a good idea to take longer words out of a dictionary – or even use an unusual name. Within a few seconds, specialized programs can try out all the words from all the dictionaries of the world. This approach is thus called a dictionary attack.
Even exotic names pose no challenge to attackers. Besides, colleagues at the workplace know your name, and personal information, like the names of your children, might also be easy for attackers to obtain. A very good password will therefore be the exact opposite of the 25 examples listed here.
However, the necessary criteria summarized in the “Secure Passwords” box would result in such entities as THw$viKiBM95K that are very hard to remember. Writing it down is not a solution because anyone with access to your desk – during your lunch break, for example – could find your notes and get into all your personal data. Fortunately, such good passwords can be created and remembered easily with the aid of mnemonic devices.
Making Sense
To begin, choose a sentence that is as long as possible but still easy to remember. This could be a quote out of a book, a rhyme, or some curious fact. The sentences should have at least 10 words and at least one number of some kind. One example could be: “Aunt Jane weighed 195 pounds before her stay at the health spa in Sedona, Arizona.” Now take the first letter of the individual words, as well as the numbers: AJw195pbhsathsiSA.
This password contains 17 characters, which is presently long enough. Furthermore, it is cryptic enough that it is not easy to guess. On the other hand, you only need to remember the sentence to remind yourself of the password. However, it doesn’t contain any symbols. In this case, it is enough simply to choose a symbol and insert it at a certain place – like a dollar sign as the fourth character, because the spa cost so much: AJw$195pbhsathsiSA. This is more than even good password-cracking programs can handle.
Some login services have problems with symbols, and spaces are especially troublesome because some programs see them as word delimiters. Internet services also sometimes swallow an ampersand (&). On the other hand, authentication routines deal with ASCII symbols between 33 (the exclamation mark) and 47 (the slash) relatively well.
Theoretically, you should now make up a separate sentence for each login service you use. To avoid having to do this, include the first character of the name of the service somewhere in the password (e.g., after the symbol). Your password for Facebook could then read something like AJw$F195pbhsathsiSA, with AJw$T195pbhsathsiSA for your Twitter account.
X Generation
If this method is too elaborate for you, then you can look for help in creating a password: Almost all distributions include the small pwgen program in their repositories, which you can install with the package manager. When opened in a terminal window, it offers a battery of possible passwords from which to select. Simply select the one from the list that you like best or that reminds you of another word. Pwgen makes sure all its suggestions are relatively easy to remember, even if it doesn’t appear to be so at first glance (Figure 1).
In practice, Pwgen passwords are surprisingly easy to internalize. With default settings, Pwgen delivers passwords with eight characters. To generate longer variations, simply enter the desired number of characters as a parameter and add symbols with the -y switch. The setting pwgen -y 12 thus generates passwords with 12 characters that contain at least one symbol.
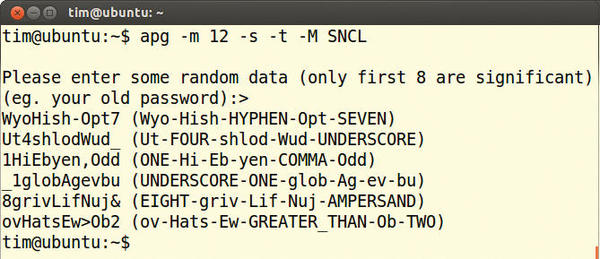
The Automated Password Generator APG is an alternative to Pwgen. After entering apg on the command line, you are prompted to enter any (random) sequence of characters, which could be your old password, as APG suggests. These characters “seed” the APG calculations and increases the security of the passwords thus generated. APG also provides phonetic transcriptions in curly brackets, which can help you remember the respective password more easily. APG also defaults to eight-characters. For longer passwords, enter a command like this:
$ apg -m 12 -s -t -M SNCL
Here, -m 12 stipulates a length of at least 12 characters. With -s, APG requests another seed, and -t calls up pronunciations for the words. The -M SNCL parameter makes sure that each password contains symbols (S), numbers (N), capital letters (C), and lowercase letters (L) (Figure 2).
If you prefer a graphical interface, your best choice would be the Java Password Generator. Because it is written in Java, you must first install the Java Runtime Environment via the package manager. Then, download the current version of the Java Password Generator, unzip the archive, and start the script with:
javaPwordGen.sh
Under Character Set in the new window (Figure 3), select Alpha-Numeric Easy to Read, type a few symbols in the field Include Characters, set the value of Length of Password to 12, and click the Generate button. Some suggestions will appear in the large pane on the right.
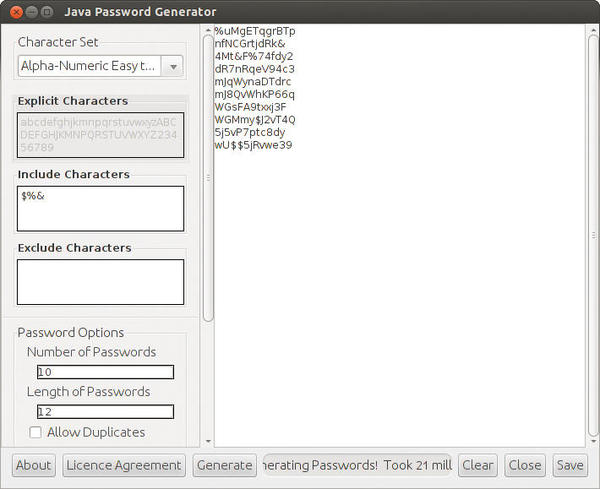 Figure 3: The Java Password Generator is one of the few password generators that offers a graphical interface.
Figure 3: The Java Password Generator is one of the few password generators that offers a graphical interface.
Besides the three password generators presented here, several others follow the same principles, such as Makepasswd or Jpwgen. However, you should stay away from Gpw, which is found in many Debian distributions: It is from 1994 and only uses lowercase letters.
Controller
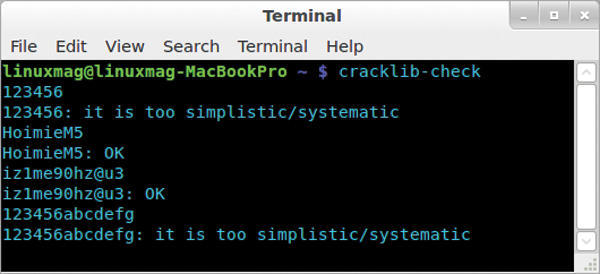
Just how secure a chosen password is can be checked with the command-line program cracklib-check. It is a part of the cracklib-runtime package under Ubuntu, in openSUSE, it is hidden in the cracklib package. After starting Cracklib-check, it at first appears as if nothing happens. However, simply type in the password you want to check and press the Enter key. Cracklib-check will then present its opinion (Figure 4).
Subsequently, you can check further passwords in the same manner. You close Cracklib-check with Ctrl+C.
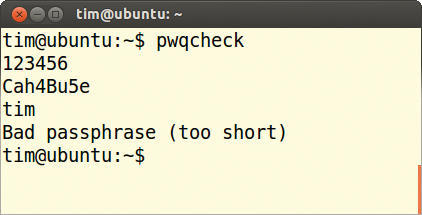
If you are going to change your password yourself and want to have it tested beforehand, you should take a look at the program pwqcheck. It is usually to be found in a package named passwdqc. Like Cracklib-check, at first nothing is displayed after opening it in a terminal window. However, just type in your current password, press Enter, type in the new password, press Enter again, and then type in your username. After pressing the Enter key once more, Pwqcheck presents its detailed assessment (Figure 5).
Many distributions allow a somewhat more elegant test; however, you must initiate the change of password yourself – even if you do not change it in the end. Under Ubuntu, call up the System Settings, click on User Accounts, click the button next to New Password, and enter the password to be tested. Directly under this field, a bar indicates how secure Ubuntu considers the password (Figure 6).
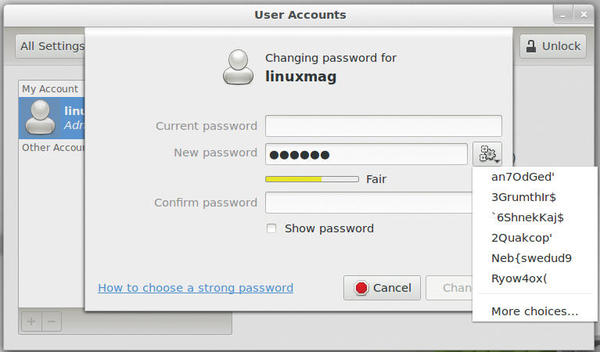 Figure 6: Although the password test in Ubuntu is quite elegant, it does not offer much information about what is wrong with a password.
Figure 6: Although the password test in Ubuntu is quite elegant, it does not offer much information about what is wrong with a password.
Ideally, the bar will turn green with the description Strong. Pressing the gear button generates more passwords, which amusingly often only achieve a Fair rating in the test. Be sure to close the window using Cancel; otherwise, you could accidentally change your password.
Unequal Treatment
KDE has a similar utility for checking passwords. From System Settings, select Password & User Account and click on Change Password. Next, you must reveal your present password. In the next window, type in the Password to be tested, and the bar immediately indicates its quality. Again, remember to click Cancel to avoid accidentally changing your password.
Astonishingly, only seldom do password management programs offer the possibility to test passwords. One of the few exceptions is KeePass. Under Ubuntu, the Mono program is found in the repositories; in other distributions, it is set up using the source code archives. After starting it with
mono KeePass.exe
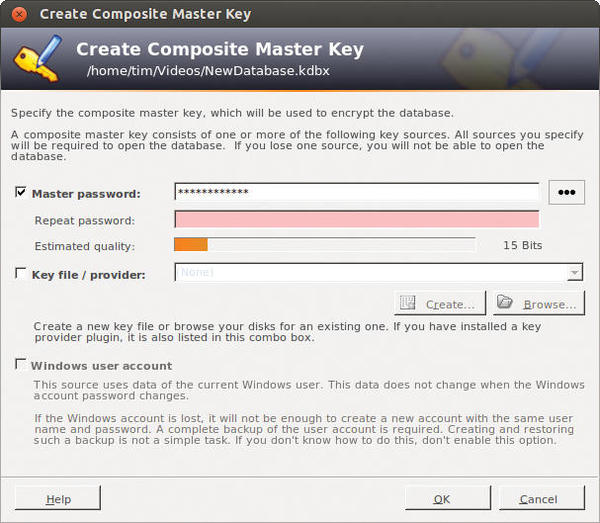
choose File | New and create a new database with any name you desire.
In the window that now appears, enter the password to be tested in the field Master password. The results of its test appear next to Estimated quality (Figure 7).
KeePass applies much more demanding standards than many of the other password test programs (e.g., Ubuntu user management). To attain a green bar, the password must be much longer, among other things.
The discrepancies between programs demonstrate a lack of agreement on a universally objective test. The result always depends on the criteria that the author of the respective test program considers necessary. Occasionally, the tests even rate as strong such simple passwords as 123456abcdef, thus leading the user to a false sense of security.
Another problem is that Linux must know your password to test it on logging into the system. Your distribution encrypts the password and stores it on the hard disk (usually in the /etc/shadow file). All Internet services also use this method, whether it be Facebook, Twitter, or Google.
To a considerable extent, the security of your password is therefore also dependent on the method of encryption used. A high-quality test for your password then would require encryption with the respective method used before an attempt to crack it. Therefore, all quality tests presented here can only provide a preliminary assessment.
Summary
A well-chosen password is half the battle, but often it travels through the Internet in plaintext like in an FTP transmission, making it easy to intercept (see the “Dangerous Internet” box). Or, the service provider might save it on its server in a readable form – something that has happened before. Even large and well-secured services are not immune to being breached: It happened to Yahoo! and GMX just this year. To ensure no attacker gains access to your passwords, you should changed them at least every three months.
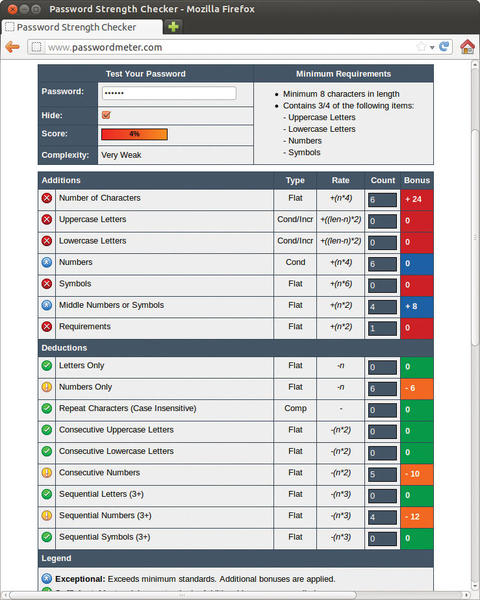 Figure 8: The Password Meter service on the Internet shows problems with a given password; however, it only communicates over an insecure connection.
Figure 8: The Password Meter service on the Internet shows problems with a given password; however, it only communicates over an insecure connection.
Sneaky colleagues don’t even need a password if you have deactivated the password request of your screensaver or activated the automatic login for the system. If the documents are not encrypted on your hard disk, a local intruder only needs to start the system from a Live system. Therefore, you should not forget any (back) doors that might be open when considering a good password.
Info
[1] Password Meter
[2] Password check by the Data Protection Officer of the Swiss Canton of Zurich (in German)
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Say Goodbye to Middle-Mouse Paste
Both Gnome and Firefox have proposed getting rid of a long-time favorite Linux feature.
-
Manjaro 26.0 Primary Desktop Environments Default to Wayland
If you want to stick with X.Org, you'll be limited to the desktop environments you can choose.
-
Mozilla Plans to AI-ify Firefox
With a new CEO in control, Mozilla is doubling down on a strategy of trust, all the while leaning into AI.
-
Gnome Says No to AI-Generated Extensions
If you're a developer wanting to create a new Gnome extension, you'd best set aside that AI code generator, because the extension team will have none of that.
-
Parrot OS Switches to KDE Plasma Desktop
Yet another distro is making the move to the KDE Plasma desktop.
-
TUXEDO Announces Gemini 17
TUXEDO Computers has released the fourth generation of its Gemini laptop with plenty of updates.
-
Two New Distros Adopt Enlightenment
MX Moksha and AV Linux 25 join ranks with Bodhi Linux and embrace the Enlightenment desktop.
-
Solus Linux 4.8 Removes Python 2
Solus Linux 4.8 has been released with the latest Linux kernel, updated desktops, and a key removal.
-
Zorin OS 18 Hits over a Million Downloads
If you doubt Linux isn't gaining popularity, you only have to look at Zorin OS's download numbers.
-
TUXEDO Computers Scraps Snapdragon X1E-Based Laptop
Due to issues with a Snapdragon CPU, TUXEDO Computers has cancelled its plans to release a laptop based on this elite hardware.