Trick Attackers with Portspoof
Flytrap
ByThe Internet is a tough place to live – especially for publicly accessible computers. A small tool called Portspoof makes port scanning a real challenge for attackers.
Seasoned attackers, and even some amateur cyber-vandals, find sport in trying to scan servers and hijack them at the same time (Figure 1). Firewalls and Intrusion Detection/Prevention systems can help, but if a single tool could truly stop all potential attacks, the Internet intrusion industry wouldn’t even exist.
 Figure 1: Number of unuathorized login attempts on the author’s network in a two-month period (by country or origin).
Figure 1: Number of unuathorized login attempts on the author’s network in a two-month period (by country or origin).
A professional intrusion attempt is typically preceded by reconnaissance and scanning. Many attackers simply perform a scan, which is easily automated with tools like Nmap. An attacker who discovers a firewall and similar defensive system can often guess which ports and services are worth attacking. However, a tool called Portspoof intervenes to cause complications and confusion for the attacker. Portspoof answers port requests with a wild mix of signatures and payloads. This confusing and unwanted information slows down any attempted port scan, forcing the attacker to manually evaluate the results in a time-consuming process.
Portspoof was developed in 2012 by Piotr Duszynski, who calls his program a “Service Emulator and Frontend Exploitation Framework.” The application is available under the GPLv2 and is implemented in C++.
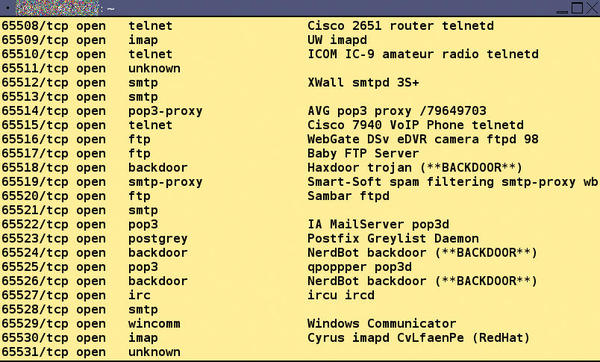
Portspoof presents various service signatures on some or all available ports, making it very difficult to discover which services are actually running on the computer. The application can simulate more than 8,000 signatures and has the ability to throw a couple of exploits back at the scanning computer.
When launched, Portspoof only listens on one port (port 4444 by default). All other ports, where attackers fall for the trap, are redirected using an iptables rule.
Installation
Portspoof is currently available in version ++1.0. Download the tool as a ZIP archive or via Git (Listing 1).
Listing 1: Getting Portspoof with Git
$ git clone https://github.com/drk1wi/portspoof.git $ ./configure && make && sudo make install
After unzipping or cloning, change to the directory created in the process, portspoof[-master]; then install the application in the three normal steps (Listing 1, line 2). By default, Portspoof ends up in /usr/local/. To define a different target directory, pass the --prefix parameter into ./configure, along with your directory choice.
After the install, quickly run portspoof -h to check whether everything has worked out so far. If everything is working, you can now run Portspoof.
Gluing and Sticking
Before launching Portspoof, you must tell iptables which ports you want to be “sticky” in the future. To let all ports join in with the fun, use the following directive:
# iptables -t nat -A PREROUTING -i eth0 -p tcp -mtcp --dport 1:65535 -j REDIRECT --to-ports 4444
However, if you are running some genuine services on the computer, omit the matching ports using the --dport option with --match multiport --dports. For example, the following command forwards all ports except 22 and 80:
# iptables -t nat -A PREROUTING -i eth0 -p tcp -m tcp -m multiport --dports 1:21,23:79,81:65535 -j REDIRECT --to-ports 4444
The iptables multiport feature can handle a maximum of 15 port ranges. If you have a busy server – like the ones used in small businesses that serve everything from DNS, FTP, SSH, mail, web, and file sharing – you might need a small loop to conveniently set up and manage the IP ranges.
An example is provided in set-spoofports.sh (Listing 2). You need to make the script executable with chmod 755 set-spoofports.sh to execute it conveniently. Then, you can use iptables -L -t nat to check afterwards whether the firewall rules are registered.
Listing 2: set-spoofports.sh
01 # set-spoofports.sh
02 # Firewall rules for Portspoof
03 #! /bin/bash
04
05 # Ports 20-22, 25, 53, 80, 110, 111, 123, 443, 465, 587, 892, 2049, 8080, 32803 are "legitimate", all others are "sticky"
06 spoofPorts="1:19 23:24 26:52 54:79 81:109 112:122 124:442 444:464 466:586 588:891 893:2048 2050:8079 8081:32800 32801:65535"
07
08 for prange in ${spoofPorts}; do
09 iptables -t nat -A PREROUTING -i eth0 -p tcp -m tcp --dport ${prange} -j REDIRECT --to-ports 4444
10 doneOnce iptables is forwarding all the ports to the target port, you can launch Portspoof. This small tool offers a useful feature set. For example, you can switch Portspoof to verbose mode with the -v option and listen in live when a “visitor” drops by. Alternatively, you can start the program as a daemon that performs its work in the background using the with -D option.
If you call Portspoof without any additional parameters, it works in what is known as open port mode. As the name suggests, open port mode means that Portspoof only shows all forwarded ports as open. That’s a nice tick, but you can do much nastier things, too. For example, why not try the following command?
# portspoof -c /<path/to>/portspoof.conf -s /<path/to>/portspoof_signatures -D
The Service Emulator now responds to requests with heaps of signatures or even exploits, which greatly complicate the attacker’s task of evaluating the results (Figure 2). Both portspoof.conf, as well as portspoof_signatures, reside by default in /usr/local/etc. The portspoof_signatures file contains prepared signatures.
Little Tricks
The portspoof.conf can be populated with signatures and even exploits that Portspoof then delivers when a remote entity queries a specific port or port range. The specification of the signature file typically suffices; you only need portspoof.conf to output precisely defined feedback for selected ports.
In portspoof.conf, you enter (line by line) the port for which the content (“payload”) is intended. The payload can be simple ASCII words, but also hexadecimal characters or regular expressions. Even exploits can be returned (caution: see the “Computer Sabotage” box). The default portspoof.conf is well commented by the Portspoof developer, which makes it easy to add your own messages and niceties.
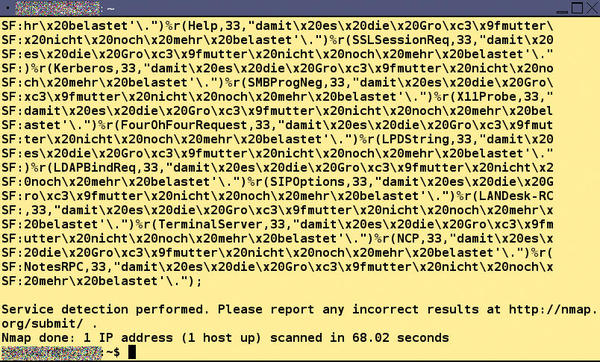
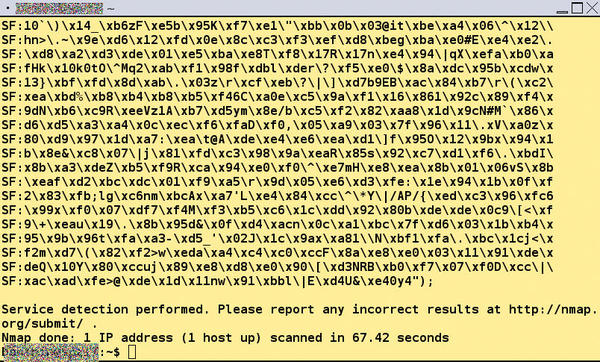
This is by no means the end of the fun for the target of the scan. Piotr Duszynski seems to have developed Portspoof under the motto that nothing is unfriendly enough for attackers, and therefore built in several additional fuzzing functions. For example, you can return several payloads specified in a file to an individual port or even generate completely arbitrary payloads in queries. A call to portspoof -f /<path/to>/redridinghood.txt -D treats the scanner to a rendition of the fairy tale “Little Red Riding Hood” – known as “Little Red Cap” in the German version (Figure 3) – and portspoof -1 -D would generate random signatures (Figure 4).
Enable another fuzzer by adding -1 or -f /<path>/text.txt with -n /<path>/signature_name.txt to a signature file. Now Portspoof not only provides entertaining, instructive, or motley payloads, but additionally adds services for signatures that you actually might encounter in the wild (Figure 5).
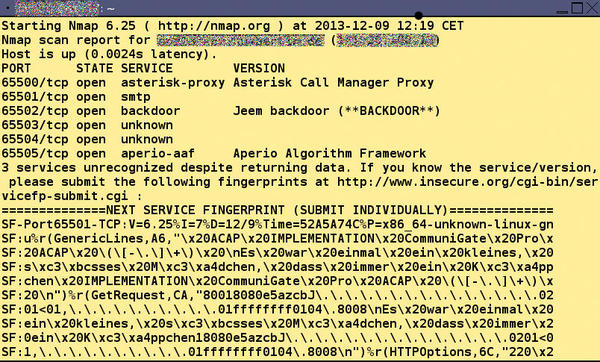
By returning arbitrary or predefined signatures and payloads, Portspoof significantly slows down a network scanner. With the service emulation alone, the time for a scan of the entire port range in the test was just under 10 hours (Figure 6); without Portspoof, it would have been done in just over 90 seconds. If you bring fuzzing into play, an attacker needs even more patience; a scan of all ports can take 30 hours or more.
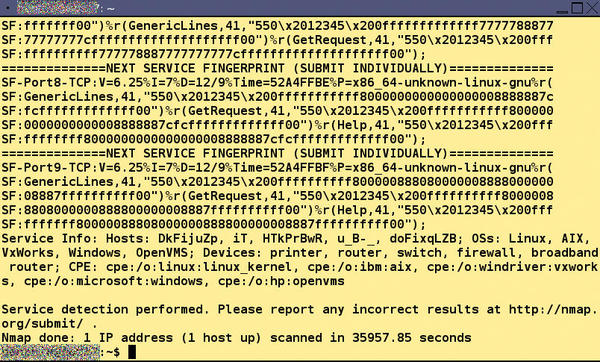 Figure 6: The port scanner Nmap needed nearly 10 hours to scan the entire port range with Portspoof running in service emulation mode. Typically, Nmap would complete such a scan in one or two minutes.
Figure 6: The port scanner Nmap needed nearly 10 hours to scan the entire port range with Portspoof running in service emulation mode. Typically, Nmap would complete such a scan in one or two minutes.
More Features
In addition to the features already described, Portspoof also lets you log any scans it detects. Just add the -l /<path>/logfile parameter when you launch Portspoof. This is not strictly necessarily, because by default the application logs all activities in /var/log/syslog. To save resources, disable syslog logging using the -D parameter.
The parameters -p port and -i IP let you define the port and IP address on which Portspoof will accept requests. To automatically load Portspoof at system startup time, Piotr Duszynski also delivers an init script in the system_files directory of the source directory tree. You might need to adapt the standard portspoof.sh file, and you will definitely need to copy it to the right /etc/rc_runlevel.d directory. Portspoof usually launches with service emulation and custom payloads.
Portspoof runs smoothly most of the time; because it is still a fairly young program, however, it has not yet been sufficiently tested in all combinations and facets. For example, Portspoof repeatedly crashed in our test during fuzzing with Red Riding Hood and signatures, while it easily carried out its work with random payloads and service signatures. It makes sense to set up a cronjob that periodically checks whether the daemon is still running and optionally notifies the admin or restarts Portspoof if necessary.
Conclusions
In Portspoof is a fine little program that can be a tough and potentially infinite quagmire for port scanners. The installation and setup are simple; the service emulator uses hardly any system resources in operation, and the sample files and scripts take much of the configuration work off the user’s shoulders. The already-extensive signature database is likely to grow as more users discover the program and start to add to the collection.
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Chaos Comes to KDE in KaOS
KaOS devs are making a major change to the distribution, and it all comes down to one system.
-
New Linux Botnet Discovered
The SSHStalker botnet uses IRC C2 to control systems via legacy Linux kernel exploits.
-
The Next Linux Kernel Turns 7.0
Linus Torvalds has announced that after Linux kernel 6.19, we'll finally reach the 7.0 iteration stage.
-
Linux From Scratch Drops SysVinit Support
LFS will no longer support SysVinit.
-
LibreOffice 26.2 Now Available
With new features, improvements, and bug fixes, LibreOffice 26.2 delivers a modern, polished office suite without compromise.
-
Linux Kernel Project Releases Project Continuity Document
What happens to Linux when there's no Linus? It's a question many of us have asked over the years, and it seems it's also on the minds of the Linux kernel project.
-
Mecha Systems Introduces Linux Handheld
Mecha Systems has revealed its Mecha Comet, a new handheld computer powered by – you guessed it – Linux.
-
MX Linux 25.1 Features Dual Init System ISO
The latest release of MX Linux caters to lovers of two different init systems and even offers instructions on how to transition.
-
Photoshop on Linux?
A developer has patched Wine so that it'll run specific versions of Photoshop that depend on Adobe Creative Cloud.
-
Linux Mint 22.3 Now Available with New Tools
Linux Mint 22.3 has been released with a pair of new tools for system admins and some pretty cool new features.